Some years ago an article appeared in the Harvard Business Review entitled “What’s Your Data Strategy?” by Leandro DalleMule and Thomas H. Davenport.
The article presents a framework for organizations to develop effective data management strategies, emphasizing the importance of distinguishing between defensive and offensive data uses.
Several topics were covered, from data access and control through breaches, usage patterns and strategies for data governance. In light of the current data privacy climate, that article’s insights remain highly relevant, albeit with some evolving nuances.
DalleMule and Davenport suggested that more than two thirds of employees often have access to data they should not despite increasing regulations. Data Breaches continue seemingly unabated, and high-profile breaches continue to make headlines. Although there is a lot of structured data in organizations, less than half is actively used in decision-making. The framework proposed in the article where compliance and risk management are respected alongside driving business growth remains pertinent today, but necessitates a more pronounced emphasis on ethical data use and consumer trust, critical traits in maintaining a positive brand reputation.
Pretectum’s Customer Master Data Management (CMDM) can play a significant role in both defensive and offensive data strategies, particularly in managing customer data effectively.
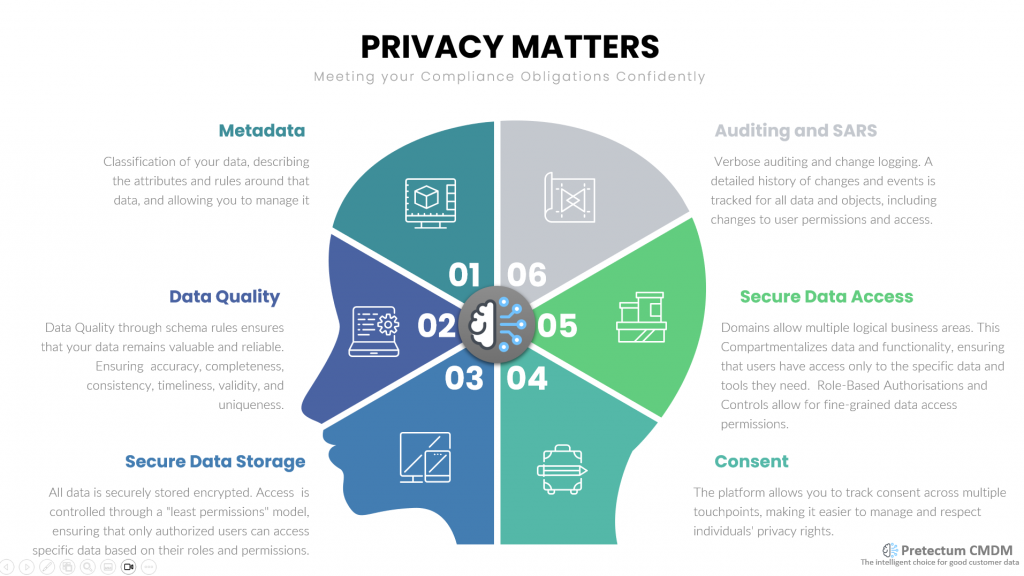
Defensive Strategies
In the context of defensive strategies, Pretectum CMDM focuses on:
- Data Accuracy and Integrity: By centralizing customer data, Pretectum ensures a reliable single source of truth. This minimizes errors and discrepancies, which is crucial for compliance with data protection regulations and maintaining data quality.
- Data Governance: Pretectum CMDM emphasizes strong governance practices, which help organizations manage data privacy risks and ensure adherence to legal requirements. This includes implementing policies for data access and usage, thereby enhancing overall data security.
- Risk Mitigation: The platform aids in identifying and addressing vulnerabilities in data management processes, helping organizations to protect sensitive information from breaches and unauthorized access.
Offensive Strategies
On the offensive side, Pretectum CMDM contributes by:
- Enhanced Decision-Making: With accurate and comprehensive customer data, organizations can leverage insights around data quality, duplicates and cross source search for strategic decision-making, improving marketing effectiveness and customer engagement strategies.
- Data Utilization for Growth: By enabling better data integration and analysis, Pretectum CMDM supports organizations in using their data proactively to identify new opportunities and drive business growth, thus aligning with offensive data strategies.
- Customer Experience Improvement: The platform helps organizations correctly recognize customers and potentially identify their preferences, integration with other technologies allows for personalized marketing and improved customer service, which can lead to increased customer loyalty and revenue.
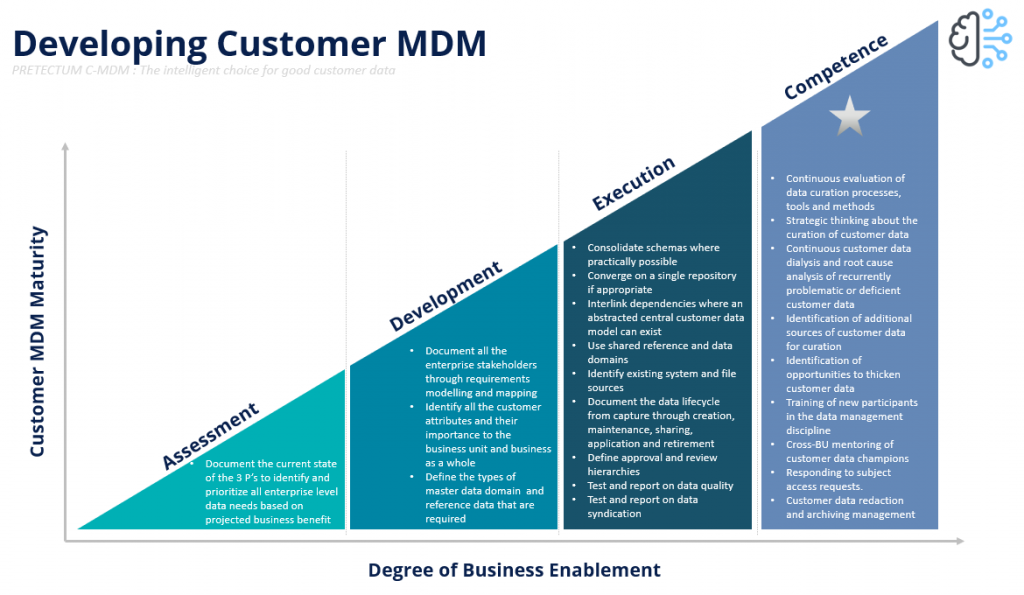
Pretectum CMDM incorporates a maturity model assessment to evaluate the effectiveness of an organization’s data management practices. This model typically follows a structured framework similar to the Capability Maturity Model (CMM), which includes:
- Initial: Ad hoc and unstructured data management practices.
- Repeatable: Basic processes are established, allowing for some consistency in data management.
- Defined: Standardized processes are documented and followed across the organization.
- Managed: Data management processes are quantitatively understood and controlled, with metrics in place to assess performance.
- Optimizing: Continuous improvement practices are implemented, leveraging feedback and innovative technologies to enhance data management capabilities.
Undertaking a maturity model assessment enables organizations to identify their current standing in data management and develop a roadmap for improvement, ensuring that both defensive and offensive strategies are effectively supported by robust data practices. Pretectum CMDM can bridge defensive and offensive data strategies by ensuring data accuracy and security while also enabling organizations to leverage their data for competitive advantage. This dual approach is essential in today’s data-driven landscape, where both compliance and innovation are critical for success.
Contact us to learn more about how we can help


